Use an External OIDC Identity Provider
We support only the OpenID Connect (OIDC) Identity Providers that expose the OpenID configuration document (for example, Google, Okta, or Auth0).
To find out whether your OIDC Identity Provider does that, check whether the following URL exists:
https://<your-issuer-url>/.well-known/openid-configuration
For users of GoodData Cloud, please note that not all OIDC providers are available by default, see Supported OIDC Identity Providers in GoodData Cloud.
Set up an OAuth2 Client
Note that the exact procedure depends on the client you are using.
Steps:
Create an OAuth2 client with the following configuration:
- Callback URL:
https://<organization-hostname>/login/oauth2/code/<organization-hostname> - Grant types:
ImplicitAuthorization codeRefresh token
- Claims:
nameopenidprofileoffline_access
- Callback URL:
Ensure your OIDC Identity Provider advertises
end_session_endpointat thehttps://<your-issuer-url>/.well-known/openid-configurationendpoint.This is required to support the logout action in GoodData. If your OIDC Identity Provider supports CORS configuration, add the URL of the Organization’s endpoint URL to the configuration.
When the OAuth2 client is created, follow the Update the OIDC Settings of the organization guide to copy and store the following parameters:
- The client ID
- The client secret
Update the OIDC Settings of the Organization
Use the following template to create an API request for updating the OIDC settings of the Organization:
You will have to provide the
$BOOTSTRAP_API_TOKENin the request header.
curl --request PUT \
--header "Authorization: Bearer $BOOTSTRAP_API_TOKEN" \
--header 'Content-Type: application/vnd.gooddata.api+json' \
--data '{
"data": {
"id": "alpha",
"type": "organization",
"attributes": {
"name": "Alpha Corp.",
"hostname": "analytics.alpha.example.com",
"oauthIssuerLocation": "https://<your-issuer-url>",
"oauthClientId": "<your-client-id>",
"oauthClientSecret": "<your-client-secret>"
}
}
}' https://analytics.alpha.example.com/api/v1/entities/admin/organizations/alpha
Important
Pay extra attention to the URL that you provide in the "oauthIssuerLocation" parameter. You must specify this URL exactly as it is provided by the OIDC Identity Provider. For example, if the URL provided ends with a trailing slash, keep the slash when passing the URL to the API as a value of the "oauthIssuerLocation" parameter.
Example: A sample API request for setting up authentication with the Auth0 Identity Provider
curl --request PUT \
--header 'Authorization: Bearer YWRtaW46Ym9vdHN0cmFwOk15U2VjcmV0UGFzc3dvcmQ=' \
--header 'Content-Type: application/vnd.gooddata.api+json' \
--data '{
"data": {
"id": "alpha",
"type": "organization",
"attributes": {
"name": "Alpha Corp.",
"hostname": "analytics.alpha.example.com",
"oauthIssuerLocation": "https://alpha-corp.auth0.com/",
"oauthClientId": "abcdefghijklmnopqrstuvwxyz0123",
"oauthClientSecret": "abcdefghijklmno-ABCDEFGHIJKLMNOPQRS-abcdefghi_ABCDEFG"
}
}
}' https://analytics.alpha.example.com/api/v1/entities/admin/organizations/alpha
Once you have updated the OIDC settings, map the users stored in the Identity Provider to your Organization.
Known limitations
Supported OIDC Identity Providers in GoodData Cloud
By default GoodData Cloud supports the following OIDC providers:
If you want to use a different provider, it must be specifically whitelisted first. To request a whitelisting of another OIDC provider, please contact GoodData support.
Auth0 specific notes
Auth0 Issuer has a trailing slash in its configuration. When configuring the
external OIDC provider for your organization, make sure that the oauthIssuerLocation
value ends with a trailing slash, like https://mycompany.eu.auth0.com/. Otherwise,
the authentication will not work.
Known issues with Auth0 IdP:
- Logout doesn’t work
Known issues with Google IdP:
- Logout doesn’t work
Amazon Cognito
Amazon Congnito distorts state variable that GoodData sends during the OAuth2 flow.
Redirect URL returned by Cognito is invalid and therefore Amazon Congnito can not be
used as Identity Provider for GoodData.
Troubleshooting
If you block 3rd party cookies in your browser and the domain of GoodData is different from the domain of your application - most probably, a silent login will not work. You can fix that by putting GoodData on the same domain as your application (GoodData should be on a subdomain, for example, analytics.<your-domain>.com).
Also, if your application is running in a different domain than Identity Server, you can also have a problem with a silent login. It is possible to fix that by using Okta custom URL domain or Auth0 custom URL domain.
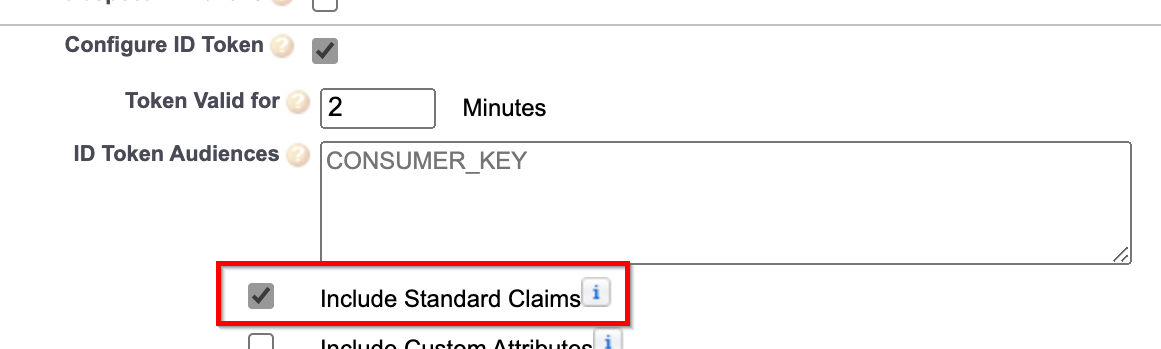
SalesForce
If you are using SalesForce as your OIDC provider, ensure that you have checked the Include Standard Claims option. Without this option, the provider will not provide the name claim in the ID token and the authentication will fail.